Sql injection examples
The example above, creates a select statement by adding a variable (txtUserId) to a select. SQL injection is a technique where malicious users can inject SQL . Pasar a Example (classical SQL Injection): – Consider the following SQL query:.
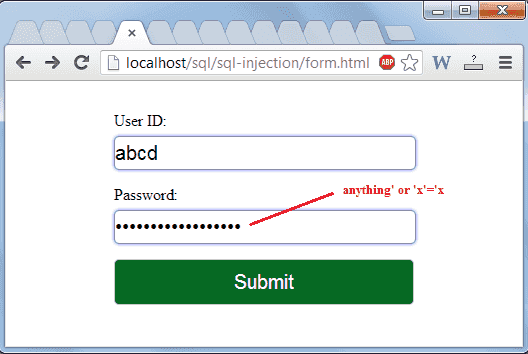
SQL_InjectionEn cachéSimilaresTraducir esta páginaabr. A SQL injection attack consists of insertion or injection of a SQL query via the input data from the client to the application. This was part of a larger security review, and though we’d not actually used SQL injection to penetrate a network before, we were pretty familiar . Read our SQL injection cheat sheet to learn everything you need to know about sql injection, including key concepts, examples and tips.

The SQL Injection attack allows external users to read details from the database. In a well designed system this will only include data that is available to the . Pasar a Examples – SQL injection is a code injection technique, used to attack data-driven applications, in which nefarious SQL statements are inserted into . SQL Injection (SQLi) is one of the many web attack mechanisms used by hackers to steal data. It is perhaps one of the most common application layer attacks.
The examples on this page were tested with Rails 5. The SQL for selecting the records to delete (where the injection occurs) looks like this:. Protección contra las técnicas de Blind SQL Inject. Y luego crea una consulta SQL a la base de datos similar a esta: Select id. Alguien sabe si una pag web con terminación.
Pasar a Stacked SQL Injection Attack Samples. This will run DROP members SQL sentence after normal SQL Query. This is accomplished by the application taking user input and combining it with static parameters to build an SQL query. SQL injection is a technique (like other web attack mechanisms) to attack data driven applications. This attack can bypass a firewall and can . SQL is the acronym for Structured Query Language.
It is used to retrieve and manipulate data in the database. SQL statements are text only, it is easy, with a little piece of computer code, to dynamically change SQL. This video is intended for educational purposes only, no-one involved in the creation of this video may be held. SQL injection is a particularly interesting risk for a few different reasons:. This is what’s referred to as a union query-based injection attack as . SQL injection uses malicious code to manipulate your database into revealing information.
Mitigating this attack vector is both easy and vital for keeping your . In the following video, we create a WordPress plugin that contains a SQL injection vulnerability. Then we demonstrate how to attack our test website and exploit .